Chapter 5 Identity
5:49pm
How did someone take over Darko’s identity?
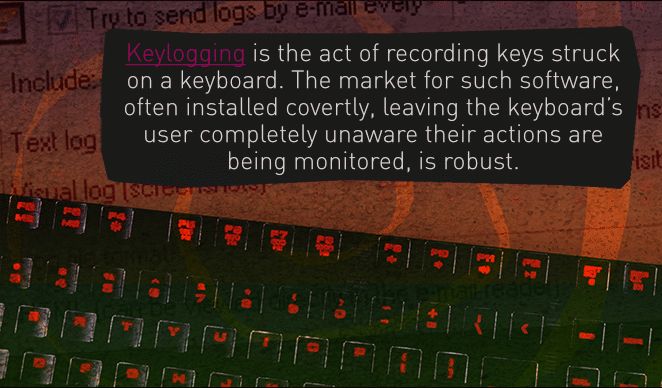
Keylogging software -- installed on his computer so everything he typed, every page he viewed, was echoed on the spying computer. But WHO installed it? And WHY?
They didn’t just steal his money, they eradicated every source of self-esteem in Darko’s life. It’s one hell of a lot of effort to destroy some kid in Kansas.
It seemed crazy and intensely personal. But maybe it was neither.
Maybe it was just practice
Practice for what?
You remember what happened next -- Idaho congressman, Jack Trask?
Of course, the married minister.
Committed suicide after his silly seductive video chats from our BoyGetsGirl.com site were posted to his Facebook page and his campaign website
He was also regular at GirlGetsBoy.com’s Avatar Club, where you can do
Anything you can imagine
As anybody you can imagine
To anybody who will agree
The Avatar club knew Jack as Big Mama Bijoux “Fat, sassy, and the ride of your life!” and Jack could not live that down. Lucky for me the story was under-reported by a respectful local press
We positioned the event as a one-off hack, perhaps a disgruntled staffer. We took some heat on our privacy settings, and YOU gave us a predictable tongue-lashing, but that was it.
I bought the disgruntled staffer.
I did pay Trask’s intern to clone his drive, and there it was again: keylogging software identical to that on Darko’s drive.
Made no sense – the same attacker, stalking a kid in Wichita and a congressman in Idaho? Or if it was the same hacker, how did he get the keylogging program on Trask’s machine? And how did he plant it on Darko’s machine? Couldn’t imagine anyone trumping through the kid’s trash to do that…
I took Darko and Trask’s drives to Artie, our Systems Analyst, and he did a full forensic analysis
And guess what
He found the keylogging software is deeply buried in the code of EVERY install of DevilsGame
The Game itself
Tracks every Player’s every move
And when and where it wants
The Game can play the Players
You discovered this catastrophic privacy and security failing and told Kazuyoshi Okada yourself?
We did. And Artie showed it to him, or tried, about 45 minutes before he died.
Does APpOCALYPSE have similar privacy and security flaws?
Dunno…but guessing yes. The scariest part is people are still “winning.”
LookU1 is still sending multimillions of Winks, harvesting multimillions of email addresses.
And people are clicking, and replying with bank or credit card info.
It is all a criminal scam then, motivated by pure greed.
Well, it’s mostly greed, but I don’t think it’s pure.
Someone used DevilsGame to socially engineer two suicides – so beyond draining data and cash, there seems to be some interest in sowing doubt and death.
In DevilsGame you created the perfect Petri dish for sin to flourish.
DevilsGame is just a game, and this is not the Game! This is a very organized entity using what we have built for data mining.
And this Entity is mining a group with a known predilection for violence, gambling and lust. Also, a group not known for their social integration.
Just this morning I saw covens of kids in Central Park playing APpOCALYPSE on their phones — cackling over gunfire and explosions! Celebrating, doing little joyous dances over murder and destruction!
Your point?
“Just a game” is being taken over with military precision. What is the intention?
I have a bad feeling.
The app itself is innocent! The violence is virtual
In APpOCALYPSE you slay imaginary enemies, but meet and share rewards with real friends.
Gate coming up. Gotta sprint.
Microsoft’s Windows 10 operating system uses keylogging software by default, tracking users’ movements unless the users disable the default settings.
The Jack Trask events echo the tragic suicide of New Orleans Pastor John Gibson after his Ashley Madison involvement was exposed in 2015.
Business News Daily defines Data Mining as “a process used to analyze raw information to try and find useful patterns and trends in it.”
Popular Mechanics explains that “Most people were introduced to the arcane world of data mining when National Security Agency contractor Edward Snowden allegedly leaked classified documents that detail how the U.S. government uses the technique to track terrorists. The security breach revealed that the government gathers billions of pieces of data—phone calls, emails, photos, and videos—from Google, Facebook, Microsoft, and other communications giants, then combs through the information for leads on national security threats… IBM estimates that humanity creates 2.5 quintillion bytes of data every day. (If these data bytes were pennies laid out flat, they would blanket the earth five times.)”

Read more on Claire Bodine's Herald Angel Blog